hashcat - 高级密码恢复工具。
用法:
hashcat [options] ... hash | hashfile | hccapxfile [dictionary | mask | directory] ...
hashcat [选项] ... hash | hashfile | hccapxfile [字典 | mask | 字典] ...
| - [options] - (选项) | ||||
|
选项短/长
|
类型
|
说明
|
例子
|
|
| -m, --hash-type | Num | Hash-type哈希类型,请参见下面的参考 | -m 1000 | |
| -a, --attack-mode | Num | Attack-mode攻击模式,请参阅下面的参考 | -a 3 | |
| -V, --version | 打印版本 | |||
| -h, --help | 打印帮助 | |||
|
--quiet
|
抑制输出 | |||
|
--hex-salt
|
假设盐是以十六进制给出的 | |||
| --hex-wordlist | 假设wordlist中的单词是以十六进制给出的 | |||
| --force | 忽略警告 | |||
| --status | 启用状态屏幕的自动更新 | |||
| --status-timer | Num | 将状态屏幕更新设置为X | --status-timer=1 | |
| --machine-readable | 以机器可读格式显示状态视图 | |||
| --keep-guessing | 在破解之后继续猜测哈希 | |||
| --loopback | 添加新的平原来导入目录 | |||
| --weak-hash-threshold | Num | 阈值X何时停止检查w | --weak=0 | |
| --markov-hcstat | File | 指定hcstat文件以使用 | --markov-hc=my.hcstat | |
| --markov-disable | 禁用马尔科夫链,模拟经典的蛮力 | |||
| --markov-classic | 启用经典马尔科夫链,没有每个位置 | |||
| -t, --markov-threshold | Num | 阈值X何时停止接受新的马尔可夫链 | -t 50 | |
| --runtime | Num | 运行时间为X秒后中止会话 | --runtime=10 | |
| --session | Str | 定义特定的会话名称 | --session=mysession | |
| --restore | 从--session恢复会话 | |||
| --restore-disable | 不要写恢复文件 | |||
| --restore-file-path | File | 恢复文件的具体路径 | --restore-file-path=my.restore | |
| -o, --outfile | File | 为恢复的散列定义outfile | -o outfile.txt | |
| --outfile-format | Num | 为恢复的散列定义outfile格式的X | --outfile-format=7 | |
| --outfile-autohex-disable | 禁止在输出平面中使用$ HEX [] | |||
| --outfile-check-timer | Num | 将outfile检查之间的秒设置为X | --outfile-check=30 | |
| -p, --separator | Char | hashlists和outfile的分隔符char | -p : | |
| --stdout | 不要破解散列,而是只打印候选 | |||
| --show | 将hashlist与potfile比较; 显示破解的哈希 | |||
| --left | 将hashlist与potfile比较; 显示未破裂的哈希 | |||
| --username | 启用忽略散列文件中的用户名 | |||
| --remove | 一旦它们被破解,就可以清除哈希值 | |||
| --remove-timer | Num | 更新输入哈希文件每X秒 | --remove-timer=30 | |
| --potfile-disable | 不要写potfile | |||
| --potfile-path | Dir | potfile的具体路径 | --potfile-path=my.pot | |
| --encoding-from | Code(代码) | 强制X |从内部词汇表编码 | --encoding-from=iso-8859-15 | |
| --encoding-to | Code | 强制内部词汇表编码到X | --encoding-to=utf-32le | |
| --debug-mode | Num | 定义调试模式(仅通过使用规则混合) | --debug-mode=4 | |
| --debug-file | File | 输出文件用于调试规则 | --debug-file=good.log | |
| --induction-dir | Dir | 指定用于回送|的归纳目录 | --induction=inducts | |
| --outfile-check-dir | Dir | 指定outfile目录来监视平原 | --outfile-check-dir=x | |
| --logfile-disable | 禁用日志文件 | |||
| --hccapx-message-pair | Num | 仅加载匹配X |的hccapx中的消息对 | --hccapx-message-pair=2 | |
| --nonce-error-corrections | Num | BF的大小范围来取代AP的随机数最后一个字节 | --nonce-error-corrections=16 | |
| --truecrypt-keyfiles | File | 要使用的密钥文件,用逗号分隔 | --truecrypt-key=x.png | |
| --veracrypt-keyfiles | File | 要使用的密钥文件,用逗号分隔 | --veracrypt-key=x.txt | |
| --veracrypt-pim | Num | VeraCrypt个人迭代multiplier | --veracrypt-pim=1000 | |
| -b, --benchmark | 运行基准 | |||
| --speed-only | 返回预期的攻击速度,然后退出 | |||
| --progress-only | 返回理想的进度步骤和时间来处理 | |||
| -c, --segment-size | 以MB为单位设置大小以从wordfile缓存到X | -c 32 | ||
| --bitmap-min | Num | 将位图允许的最小位设置为X | --bitmap-min=24 | |
| --bitmap-max | Num | 将位图允许的最大位设置为X | --bitmap-max=24 | |
| --cpu-affinity | Str | 锁定到CPU设备,用逗号分隔 | --cpu-affinity=1,2,3 | |
| -I, --opencl-info | 显示有关检测到的OpenCL平台/设备的信息 | -I | ||
| --opencl-platforms | Str | 使用OpenCL平台,用逗号分隔 | --opencl-platforms=2 | |
| -d, --opencl-devices | Str | 使用OpenCL设备,用逗号分隔 | -d 1 | |
| -D, --opencl-device-types | Str | 使用OpenCL设备类型,用逗号分隔 | -D 1 | |
| --opencl-vector-width | Num | 手动覆盖OpenCL矢量宽度到X | --opencl-vector=4 | |
| -w, --workload-profile | Num | 启用特定的工作负载配置文件,请参阅下面的池 | -w 3 | |
| -n, --kernel-accel | Num | 手动调整工作负载,将外环步长设置为X | -n 64 | |
| -u, --kernel-loops | Num | 手动调整工作负载,将内环步长设置为X | -u 256 | |
| --nvidia-spin-damp | Num | 解决方法NVIDIA?(英伟达?)CPU烧录循环错误,以百分比表示 | --nvidia-spin-damp=50 | |
| --gpu-temp-disable | 禁用温度和fanspeed读取和触发器 | |||
| --gpu-temp-abort | Num | 如果GPU温度达到X摄氏度,则中止 | --gpu-temp-abort=100 | |
| --gpu-temp-retain | Num | 尝试将GPU温度保持在X摄氏度 | --gpu-temp-retain=95 | |
| --powertune-enable | 启用功率调整。 完成|时恢复设置 | |||
| --scrypt-tmto | Num | 手动覆盖scrypt的TMTO值为X | --scrypt-tmto=3 | |
| -s, --skip | Num | 从一开始就跳过X个单词 | -s 1000000 | |
| -l, --limit | Num | 限制X字从开始+跳过的单词 | -l 1000000 | |
| --keyspace | 显示密钥空间基础:mod值并退出 | |||
| -j, --rule-left | Rule(规则) | 单词规则应用于左词表| |中的每个单词 | -j 'c' | |
| -k, --rule-right | Rule | 单词规则应用于右词表| |中的每个单词 | -k '^-' | |
| -r, --rules-file | File | 多个规则应用于来自词表|的每个词 | -r rules/best64.rule | |
| -g, --generate-rules | Num | 生成X随机规则 | -g 10000 | |
| --generate-rules-func-min | Num | 强制每个规则的最小X函数 | ||
| --generate-rules-func-max | Num | 强制每个规则的最大X个函数 | ||
| --generate-rules-seed | Num | 强制将RNG种子设置为X | ||
| -1, --custom-charset1 | CS | 用户定义的字符集?1 | -1 ?l?d?u | |
| -2, --custom-charset2 | CS | 用户定义的字符集?2 | -2 ?l?d?s | |
| -3, --custom-charset3 | CS | 用户定义的字符集?3 | ||
| -4, --custom-charset4 | CS | 用户定义的字符集?4 | ||
| -i, --increment | 启用屏蔽增量模式 | |||
| --increment-min | Num | 在X |开始掩码递增 | --increment-min=4 | |
| --increment-max | Num | 在X |处停止屏蔽递增 | --increment-max=8 | |
| - [ Hash modes ] -(哈希模式) | ||||
| # | Name名称 | Category分类 | ||
| 900 | MD4 | Raw Hash | ||
| 0 | MD5 | Raw Hash | ||
| 5100 | Half MD5 | Raw Hash | ||
| 100 | SHA1 | Raw Hash | ||
| 1300 | SHA-224 | Raw Hash | ||
| 1400 | SHA-256 | Raw Hash | ||
| 10800 | SHA-384 | Raw Hash | ||
| 1700 | SHA-512 | Raw Hash | ||
| 5000 | SHA-3 (Keccak) | Raw Hash | ||
| 600 | BLAKE2b-512 | Raw Hash | ||
| 10100 | SipHash | Raw Hash | ||
| 6000 | RIPEMD-160 | Raw Hash | ||
| 6100 | Whirlpool | Raw Hash | ||
| 6900 | GOST R 34.11-94 | Raw Hash | ||
| 11700 | GOST R 34.11-2012 (Streebog) 256-bit | Raw Hash | ||
| 11800 | GOST R 34.11-2012 (Streebog) 512-bit | Raw Hash | ||
| 10 | md5($pass.$salt) | Raw Hash, Salted and/or Iterated | ||
| 20 | md5($salt.$pass) | Raw Hash, Salted and/or Iterated | ||
| 30 | md5(utf16le($pass).$salt) | Raw Hash, Salted and/or Iterated | ||
| 40 | md5($salt.utf16le($pass)) | Raw Hash, Salted and/or Iterated | ||
| 3800 | md5($salt.$pass.$salt) | Raw Hash, Salted and/or Iterated | ||
| 3710 | md5($salt.md5($pass)) | Raw Hash, Salted and/or Iterated | ||
| 4010 | md5($salt.md5($salt.$pass)) | Raw Hash, Salted and/or Iterated | ||
| 4110 | md5($salt.md5($pass.$salt)) | Raw Hash, Salted and/or Iterated | ||
| 2600 | md5(md5($pass)) | Raw Hash, Salted and/or Iterated | ||
| 3910 | md5(md5($pass).md5($salt)) | Raw Hash, Salted and/or Iterated | ||
| 4300 | md5(strtoupper(md5($pass))) | Raw Hash, Salted and/or Iterated | ||
| 4400 | md5(sha1($pass)) | Raw Hash, Salted and/or Iterated | ||
| 110 | sha1($pass.$salt) | Raw Hash, Salted and/or Iterated | ||
| 120 | sha1($salt.$pass) | Raw Hash, Salted and/or Iterated | ||
| 130 | sha1(utf16le($pass).$salt) | Raw Hash, Salted and/or Iterated | ||
| 140 | sha1($salt.utf16le($pass)) | Raw Hash, Salted and/or Iterated | ||
| 4500 | sha1(sha1($pass)) | Raw Hash, Salted and/or Iterated | ||
| 4520 | sha1($salt.sha1($pass)) | Raw Hash, Salted and/or Iterated | ||
| 4700 | sha1(md5($pass)) | Raw Hash, Salted and/or Iterated | ||
| 4900 | sha1($salt.$pass.$salt) | Raw Hash, Salted and/or Iterated | ||
| 14400 | sha1(CX) | Raw Hash, Salted and/or Iterated | ||
| 1410 | sha256($pass.$salt) | Raw Hash, Salted and/or Iterated | ||
| 1420 | sha256($salt.$pass) | Raw Hash, Salted and/or Iterated | ||
| 1430 | sha256(utf16le($pass).$salt) | Raw Hash, Salted and/or Iterated | ||
| 1440 | sha256($salt.utf16le($pass)) | Raw Hash, Salted and/or Iterated | ||
| 1710 | sha512($pass.$salt) | Raw Hash, Salted and/or Iterated | ||
| 1720 | sha512($salt.$pass) | Raw Hash, Salted and/or Iterated | ||
| 1730 | sha512(utf16le($pass).$salt) | Raw Hash, Salted and/or Iterated | ||
| 1740 | sha512($salt.utf16le($pass)) | Raw Hash, Salted and/or Iterated | ||
| 50 | HMAC-MD5 (key = $pass) | Raw Hash, Authenticated | ||
| 60 | HMAC-MD5 (key = $salt) | Raw Hash, Authenticated | ||
| 150 | HMAC-SHA1 (key = $pass) | Raw Hash, Authenticated | ||
| 160 | HMAC-SHA1 (key = $salt) | Raw Hash, Authenticated | ||
| 1450 | HMAC-SHA256 (key = $pass) | Raw Hash, Authenticated | ||
| 1460 | HMAC-SHA256 (key = $salt) | Raw Hash, Authenticated | ||
| 1750 | HMAC-SHA512 (key = $pass) | Raw Hash, Authenticated | ||
| 1760 | HMAC-SHA512 (key = $salt) | Raw Hash, Authenticated | ||
| 14000 | DES (PT = $salt, key = $pass) | Raw Cipher, Known-Plaintext attack | ||
| 14100 | 3DES (PT = $salt, key = $pass) | Raw Cipher, Known-Plaintext attack | ||
| 14900 | Skip32 (PT = $salt, key = $pass) | Raw Cipher, Known-Plaintext attack | ||
| 15400 | ChaCha20 | Raw Cipher, Known-Plaintext attack | ||
| 400 | phpass | Generic KDF | ||
| 8900 | scrypt | Generic KDF | ||
| 11900 | PBKDF2-HMAC-MD5 | Generic KDF | ||
| 12000 | PBKDF2-HMAC-SHA1 | Generic KDF | ||
| 10900 | PBKDF2-HMAC-SHA256 | Generic KDF | ||
| 12100 | PBKDF2-HMAC-SHA512 | Generic KDF | ||
| 23 | Skype | Network Protocols | ||
| 2500 | WPA/WPA2 | Network Protocols | ||
| 4800 | iSCSI CHAP authentication, MD5(CHAP) | Network Protocols | ||
| 5300 | IKE-PSK MD5 | Network Protocols | ||
| 5400 | IKE-PSK SHA1 | Network Protocols | ||
| 5500 | NetNTLMv1 | Network Protocols | ||
| 5500 | NetNTLMv1+ESS | Network Protocols | ||
| 5600 | NetNTLMv2 | Network Protocols | ||
| 7300 | IPMI2 RAKP HMAC-SHA1 | Network Protocols | ||
| 7500 | Kerberos 5 AS-REQ Pre-Auth etype 23 | Network Protocols | ||
| 8300 | DNSSEC (NSEC3) | Network Protocols | ||
| 10200 | CRAM-MD5 | Network Protocols | ||
| 11100 | PostgreSQL CRAM (MD5) | Network Protocols | ||
| 11200 | MySQL CRAM (SHA1) | Network Protocols | ||
| 11400 | SIP digest authentication (MD5) | Network Protocols | ||
| 13100 | Kerberos 5 TGS-REP etype 23 | Network Protocols | ||
| 121 | SMF (Simple Machines Forum) > v1.1 | Forums, CMS, E-Commerce, Frameworks | ||
| 400 | phpBB3 (MD5) | Forums, CMS, E-Commerce, Frameworks | ||
| 2611 | vBulletin < v3.8.5 | Forums, CMS, E-Commerce, Frameworks | ||
| 2711 | vBulletin >= v3.8.5 | Forums, CMS, E-Commerce, Frameworks | ||
| 2811 | MyBB 1.2+ | Forums, CMS, E-Commerce, Frameworks | ||
| 2811 | IPB2+ (Invision Power Board) | Forums, CMS, E-Commerce, Frameworks | ||
| 8400 | WBB3 (Woltlab Burning Board) | Forums, CMS, E-Commerce, Frameworks | ||
| 11 | Joomla < 2.5.18 | Forums, CMS, E-Commerce, Frameworks | ||
| 400 | Joomla >= 2.5.18 (MD5) | Forums, CMS, E-Commerce, Frameworks | ||
| 400 | WordPress (MD5) | Forums, CMS, E-Commerce, Frameworks | ||
| 2612 | PHPS | Forums, CMS, E-Commerce, Frameworks | ||
| 7900 | Drupal7 | Forums, CMS, E-Commerce, Frameworks | ||
| 21 | osCommerce | Forums, CMS, E-Commerce, Frameworks | ||
| 21 | xt:Commerce | Forums, CMS, E-Commerce, Frameworks | ||
| 11000 | PrestaShop | Forums, CMS, E-Commerce, Frameworks | ||
| 124 | Django (SHA-1) | Forums, CMS, E-Commerce, Frameworks | ||
| 10000 | Django (PBKDF2-SHA256) | Forums, CMS, E-Commerce, Frameworks | ||
| 3711 | MediaWiki B type | Forums, CMS, E-Commerce, Frameworks | ||
| 13900 | OpenCart | Forums, CMS, E-Commerce, Frameworks | ||
| 4521 | Redmine | Forums, CMS, E-Commerce, Frameworks | ||
| 4522 | PunBB | Forums, CMS, E-Commerce, Frameworks | ||
| 12001 | Atlassian (PBKDF2-HMAC-SHA1) | Forums, CMS, E-Commerce, Frameworks | ||
| 12 | PostgreSQL | Database Server | ||
| 131 | MSSQL (2000) | Database Server | ||
| 132 | MSSQL (2005) | Database Server | ||
| 1731 | MSSQL (2012, 2014) | Database Server | ||
| 200 | MySQL323 | Database Server | ||
| 300 | MySQL4.1/MySQL5 | Database Server | ||
| 3100 | Oracle H: Type (Oracle 7+) | Database Server | ||
| 112 | Oracle S: Type (Oracle 11+) | Database Server | ||
| 12300 | Oracle T: Type (Oracle 12+) | Database Server | ||
| 8000 | Sybase ASE | Database Server | ||
| 141 | Episerver 6.x < .NET 4 | HTTP, SMTP, LDAP Server | ||
| 1441 | Episerver 6.x >= .NET 4 | HTTP, SMTP, LDAP Server | ||
| 1600 | Apache $apr1$ MD5, md5apr1, MD5 (APR) | HTTP, SMTP, LDAP Server | ||
| 12600 | ColdFusion 10+ | HTTP, SMTP, LDAP Server | ||
| 1421 | hMailServer | HTTP, SMTP, LDAP Server | ||
| 101 | nsldap, SHA-1(Base64), Netscape LDAP SHA | HTTP, SMTP, LDAP Server | ||
| 111 | nsldaps, SSHA-1(Base64), Netscape LDAP SSHA | HTTP, SMTP, LDAP Server | ||
| 1411 | SSHA-256(Base64), LDAP {SSHA256} | HTTP, SMTP, LDAP Server | ||
| 1711 | SSHA-512(Base64), LDAP {SSHA512} | HTTP, SMTP, LDAP Server | ||
| 15000 | FileZilla Server >= 0.9.55 | FTP Server | ||
| 11500 | CRC32 | Checksums | ||
| 3000 | LM | Operating Systems | ||
| 1000 | NTLM | Operating Systems | ||
| 1100 | Domain Cached Credentials (DCC), MS Cache | Operating Systems | ||
| 2100 | Domain Cached Credentials 2 (DCC2), MS Cache 2 | Operating Systems | ||
| 15300 | DPAPI masterkey file v1 and v2 | Operating Systems | ||
| 12800 | MS-AzureSync PBKDF2-HMAC-SHA256 | Operating Systems | ||
| 1500 | descrypt, DES (Unix), Traditional DES | Operating Systems | ||
| 12400 | BSDi Crypt, Extended DES | Operating Systems | ||
| 500 | md5crypt, MD5 (Unix), Cisco-IOS $1$ (MD5) | Operating Systems | ||
| 3200 | bcrypt $2*$, Blowfish (Unix) | Operating Systems | ||
| 7400 | sha256crypt $5$, SHA256 (Unix) | Operating Systems | ||
| 1800 | sha512crypt $6$, SHA512 (Unix) | Operating Systems | ||
| 122 | OSX v10.4, OSX v10.5, OSX v10.6 | Operating Systems | ||
| 1722 | OSX v10.7 | Operating Systems | ||
| 7100 | OSX v10.8+ (PBKDF2-SHA512) | Operating Systems | ||
| 6300 | AIX {smd5} | Operating Systems | ||
| 6700 | AIX {ssha1} | Operating Systems | ||
| 6400 | AIX {ssha256} | Operating Systems | ||
| 6500 | AIX {ssha512} | Operating Systems | ||
| 2400 | Cisco-PIX MD5 | Operating Systems | ||
| 2410 | Cisco-ASA MD5 | Operating Systems | ||
| 500 | Cisco-IOS $1$ (MD5) | Operating Systems | ||
| 5700 | Cisco-IOS type 4 (SHA256) | Operating Systems | ||
| 9200 | Cisco-IOS $8$ (PBKDF2-SHA256) | Operating Systems | ||
| 9300 | Cisco-IOS $9$ (scrypt) | Operating Systems | ||
| 22 | Juniper NetScreen/SSG (ScreenOS) | Operating Systems | ||
| 501 | Juniper IVE | Operating Systems | ||
| 15100 | Juniper/NetBSD sha1crypt | Operating Systems | ||
| 7000 | FortiGate (FortiOS) | Operating Systems | ||
| 5800 | Samsung Android Password/PIN | Operating Systems | ||
| 13800 | Windows Phone 8+ PIN/password | Operating Systems | ||
| 8100 | Citrix NetScaler | Operating Systems | ||
| 8500 | RACF | Operating Systems | ||
| 7200 | GRUB 2 | Operating Systems | ||
| 9900 | Radmin2 | Operating Systems | ||
| 125 | ArubaOS | Operating Systems | ||
| 7700 | SAP CODVN B (BCODE) | Enterprise Application Software (EAS) | ||
| 7800 | SAP CODVN F/G (PASSCODE) | Enterprise Application Software (EAS) | ||
| 10300 | SAP CODVN H (PWDSALTEDHASH) iSSHA-1 | Enterprise Application Software (EAS) | ||
| 8600 | Lotus Notes/Domino 5 | Enterprise Application Software (EAS) | ||
| 8700 | Lotus Notes/Domino 6 | Enterprise Application Software (EAS) | ||
| 9100 | Lotus Notes/Domino 8 | Enterprise Application Software (EAS) | ||
| 133 | PeopleSoft | Enterprise Application Software (EAS) | ||
| 13500 | PeopleSoft PS_TOKEN | Enterprise Application Software (EAS) | ||
| 11600 | 7-Zip | Archives | ||
| 12500 | RAR3-hp | Archives | ||
| 13000 | RAR5 | Archives | ||
| 13200 | AxCrypt | Archives | ||
| 13300 | AxCrypt in-memory SHA1 | Archives | ||
| 13600 | WinZip | Archives | ||
| 14700 | iTunes backup < 10.0 | Archives | ||
| 14800 | iTunes backup >= 10.0 | Archives | ||
| 62XY | TrueCrypt | Full-Disk Encryption (FDE) | ||
| X | 1 = PBKDF2-HMAC-RIPEMD160 | Full-Disk Encryption (FDE) | ||
| X | 2 = PBKDF2-HMAC-SHA512 | Full-Disk Encryption (FDE) | ||
| X | 3 = PBKDF2-HMAC-Whirlpool | Full-Disk Encryption (FDE) | ||
| X | 4 = PBKDF2-HMAC-RIPEMD160 + boot-mode | Full-Disk Encryption (FDE) | ||
| Y | 1 = XTS 512 bit pure AES | Full-Disk Encryption (FDE) | ||
| Y | 1 = XTS 512 bit pure Serpent | Full-Disk Encryption (FDE) | ||
| Y | 1 = XTS 512 bit pure Twofish | Full-Disk Encryption (FDE) | ||
| Y | 2 = XTS 1024 bit pure AES | Full-Disk Encryption (FDE) | ||
| Y | 2 = XTS 1024 bit pure Serpent | Full-Disk Encryption (FDE) | ||
| Y | 2 = XTS 1024 bit pure Twofish | Full-Disk Encryption (FDE) | ||
| Y | 2 = XTS 1024 bit cascaded AES-Twofish | Full-Disk Encryption (FDE) | ||
| Y | 2 = XTS 1024 bit cascaded Serpent-AES | Full-Disk Encryption (FDE) | ||
| Y | 2 = XTS 1024 bit cascaded Twofish-Serpent | Full-Disk Encryption (FDE) | ||
| Y | 3 = XTS 1536 bit all | Full-Disk Encryption (FDE) | ||
| 8800 | Android FDE <= 4.3 | Full-Disk Encryption (FDE) | ||
| 12900 | Android FDE (Samsung DEK) | Full-Disk Encryption (FDE) | ||
| 12200 | eCryptfs | Full-Disk Encryption (FDE) | ||
| 137XY | VeraCrypt | Full-Disk Encryption (FDE) | ||
| X | 1 = PBKDF2-HMAC-RIPEMD160 | Full-Disk Encryption (FDE) | ||
| X | 2 = PBKDF2-HMAC-SHA512 | Full-Disk Encryption (FDE) | ||
| X | 3 = PBKDF2-HMAC-Whirlpool | Full-Disk Encryption (FDE) | ||
| X | 4 = PBKDF2-HMAC-RIPEMD160 + boot-mode | Full-Disk Encryption (FDE) | ||
| X | 5 = PBKDF2-HMAC-SHA256 | Full-Disk Encryption (FDE) | ||
| X | 6 = PBKDF2-HMAC-SHA256 + boot-mode | Full-Disk Encryption (FDE) | ||
| Y | 1 = XTS 512 bit pure AES | Full-Disk Encryption (FDE) | ||
| Y | 1 = XTS 512 bit pure Serpent | Full-Disk Encryption (FDE) | ||
| Y | 1 = XTS 512 bit pure Twofish | Full-Disk Encryption (FDE) | ||
| Y | 2 = XTS 1024 bit pure AES | Full-Disk Encryption (FDE) | ||
| Y | 2 = XTS 1024 bit pure Serpent | Full-Disk Encryption (FDE) | ||
| Y | 2 = XTS 1024 bit pure Twofish | Full-Disk Encryption (FDE) | ||
| Y | 2 = XTS 1024 bit cascaded AES-Twofish | Full-Disk Encryption (FDE) | ||
| Y | 2 = XTS 1024 bit cascaded Serpent-AES | Full-Disk Encryption (FDE) | ||
| Y | 2 = XTS 1024 bit cascaded Twofish-Serpent | Full-Disk Encryption (FDE) | ||
| Y | 3 = XTS 1536 bit all | Full-Disk Encryption (FDE) | ||
| 14600 | LUKS | Full-Disk Encryption (FDE) | ||
| 9700 | MS Office <= 2003 $0/$1, MD5 + RC4 | Documents | ||
| 9710 | MS Office <= 2003 $0/$1, MD5 + RC4, collider #1 | Documents | ||
| 9720 | MS Office <= 2003 $0/$1, MD5 + RC4, collider #2 | Documents | ||
| 9800 | MS Office <= 2003 $3/$4, SHA1 + RC4 | Documents | ||
| 9810 | MS Office <= 2003 $3, SHA1 + RC4, collider #1 | Documents | ||
| 9820 | MS Office <= 2003 $3, SHA1 + RC4, collider #2 | Documents | ||
| 9400 | MS Office 2007 | Documents | ||
| 9500 | MS Office 2010 | Documents | ||
| 9600 | MS Office 2013 | Documents | ||
| 10400 | PDF 1.1 - 1.3 (Acrobat 2 - 4) | Documents | ||
| 10410 | PDF 1.1 - 1.3 (Acrobat 2 - 4), collider #1 | Documents | ||
| 10420 | PDF 1.1 - 1.3 (Acrobat 2 - 4), collider #2 | Documents | ||
| 10500 | PDF 1.4 - 1.6 (Acrobat 5 - 8) | Documents | ||
| 10600 | PDF 1.7 Level 3 (Acrobat 9) | Documents | ||
| 10700 | PDF 1.7 Level 8 (Acrobat 10 - 11) | Documents | ||
| 9000 | Password Safe v2 | Password Managers | ||
| 5200 | Password Safe v3 | Password Managers | ||
| 6800 | LastPass + LastPass sniffed | Password Managers | ||
| 6600 | 1Password, agilekeychain | Password Managers | ||
| 8200 | 1Password, cloudkeychain | Password Managers | ||
| 11300 | Bitcoin/Litecoin wallet.dat | Password Managers | ||
| 12700 | Blockchain, My Wallet | Password Managers | ||
| 15200 | Blockchain, My Wallet, V2 | Password Managers | ||
| 13400 | KeePass 1 (AES/Twofish) and KeePass 2 (AES) | Password Managers | ||
| 15500 | JKS Java Key Store Private Keys (SHA1) | Password Managers | ||
| 15600 | Ethereum Wallet, PBKDF2-HMAC-SHA256 | Password Managers | ||
| 15700 | Ethereum Wallet, SCRYPT | Password Managers | ||
| 99999 | Plaintext | Plaintext | ||
| - [ Outfile Formats ] -文件输出格式 | ||||
| # | Format | |||
| 1 | hash[:salt] | |||
| 2 | plain | |||
| 3 | hash[:salt]:plain | |||
| 4 | hex_plain | |||
| 5 | hash[:salt]:hex_plain | |||
| 6 | plain:hex_plain | |||
| 7 | hash[:salt]:plain:hex_plain | |||
| 8 | crackpos | |||
| 9 | hash[:salt]:crack_pos | |||
| 10 | plain:crack_pos | |||
| 11 | hash[:salt]:plain:crack_pos | |||
| 12 | hex_plain:crack_pos | |||
| 13 | hash[:salt]:hex_plain:crack_pos | |||
| 14 | plain:hex_plain:crack_pos | |||
| 15 | hash[:salt]:plain:hex_plain:crack_pos | |||
| - [ Rule Debugging Modes ] -规则调试模式 | ||||
| # | Format | |||
| 1 | Finding-Rule | |||
| 2 | Original-Word | |||
| 3 | Original-Word:Finding-Rule | |||
| 4 | Original-Word:Finding-Rule:Processed-Word | |||
| - [ Attack Modes ] -攻击模式 | ||||
| # | Mode | |||
| 0 | Straight | |||
| 1 | Combination | |||
| 3 | Brute-force | |||
| 6 | Hybrid Wordlist + Mask | |||
| 7 | Hybrid Mask + Wordlist | |||
| - [ Built-in Charsets ] -内置字符集 | ||||
| ? | Charset | |||
| l | abcdefghijklmnopqrstuvwxyz | |||
| u | ABCDEFGHIJKLMNOPQRSTUVWXYZ | |||
| d | 0123456789 | |||
| h | 0123456789abcdef | |||
| H | 0123456789ABCDEF | |||
| s | !"#$%&'()*+,-./:;<=>?@[\]^_`{|}~ | |||
| a | ?l?u?d?s | |||
| b | 0x00 - 0xff | |||
| - [ OpenCL Device Types ] -OpenCL设备类型 | ||||
| # | Device Type | |||
| 1 | CPU | |||
| 2 | CPU | |||
| 3 | FPGA, DSP, Co-Processor | |||
| - [ Workload Profiles ] -工作量配置文件 | ||||
| # | Performance | Runtime | Power Consumption | Desktop Impact |
| 1 | Low | 2 ms | Low | Minimal |
| 2 | Default | 12 ms | Economic | Noticeable |
| 3 | High | 96 ms | High | Unresponsive |
| 4 | Nightmare | 480 ms | Insane | Headless |
| - [ Basic Examples ] -基本示例 | ||||
| Attack- Mode | Hash-Type | Example command | ||
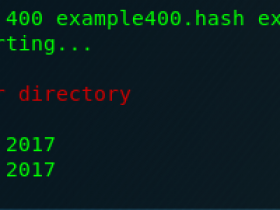
| Wordlist | $P$ | hashcat -a 0 -m 400 example400.hash example.dict | ||
| Wordlist + Rules | MD5 | hashcat -a 0 -m 0 example0.hash example.dict -r rules/best64.rule | ||
| Brute-Force | MD5 | hashcat -a 3 -m 0 example0.hash ?a?a?a?a?a?a | ||
| Combinator | MD5 | hashcat -a 1 -m 0 example0.hash example.dict example.dict | ||
hashcat效果与评价:
虽然说此软件是很强大,但是它需要一个字典表,因此就很尴尬了。
想了解更多,请查看:
* https://hashcat.net/wiki/#howtos_videos_papers_articles_etc_in_the_wild
* https://hashcat.net/faq/
下面就是没字典表的情况:
在线视频:
优酷:http://v.youku.com/v_show/id_XMzE3MTU4MzQ5Ng==.html
腾讯:https://v.qq.com/x/page/p0507g3u80h.html